Cap Walkthrough
About HackTheBox Cap Machine
Machine Creator: InfoSecJack
IP: 10.10.10.245
This is a write-up of Cap, an "easy" rated Linux machine from HackTheBox. Hack The Box is a free online platform that allows you to practice advancing your cybersecurity skills.
There are two flags to retrieve from each Hack The Box machine. The users.txt flag and the root.txt flag.
Initial Recon
The initial nmap scan tells us our target is an Ubuntu machine running an FTP server, SSH, and hosting a website on port 80.
Nmap shows us that we cannot FTP onto the box with the credentials anonymous:anonymous.
I decided to run gobuster against the site running on port 80 to brute force directories as I browsed the website manually.
The web page is hosting a network monitoring page. We can view the machine’s network interfaces by clicking the “IP Config” tab. We can also see security events such as failed login attempts, by clicking around the web UI .
We can also view other information about the server from this dashboard, such as network connections, by clicking the "Network Status" tab.
Gaining Our Foothold
Obtaining User Credentials
There is another interesting page on the site under "Security Snapshot.” On this page, we can download PCAPs(packet captures). The URL has a number parameter. By incrementing this parameter, we can enumerate through the various stored PCAPs. I downloaded four PCAP files (3,2,1,0).pcap.
To get a quick understanding of what the PCAPs may contain, I ran tcpflow against each capture and stored the results in a directory called packets. We could have also used Wireshark for this.
tcpflow is a CLI(Command Line Interface) tool that allows us to analyze network traffic and stores the results in files that we can easily grep for interesting basic information. You can read more about tcpflow from this neat, quick blog post here from techmint.
As mentioned, we can easily grep through the Tcpflow output for keywords. I first searched for credentials by grepping for “user” and “pass.”
Using Tcpflow, we find user credentials nathan:Buck3tH4TF0RM3!. The PCAP contains these captured credentials from an FTP login. So with this user, we log in via FTP and grab the user flag here.
If this machine accepts password authentication for SSH, we may gain shell access to the machine with these same credentials.
The figure above shows that we successfully can log into the machine using SSH and the credentials we extracted from the PCAP file.
Privilege Escalation
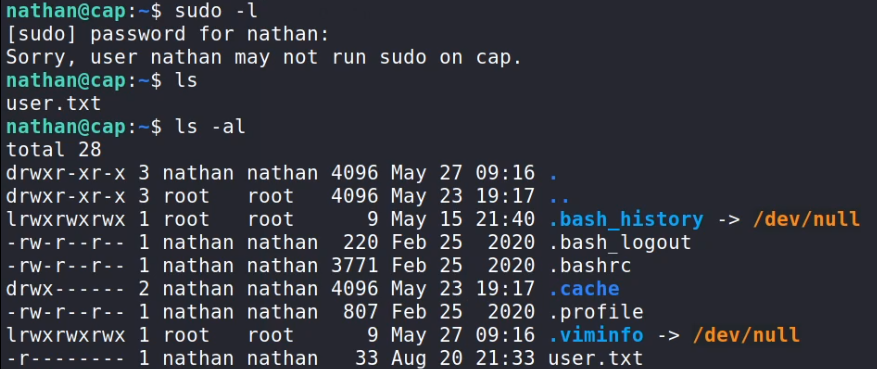
I run sudo -l to see if my user has any interesting sudo permissions. I then checked to see if any SUID binaries looked interesting. I also checked out the environment variables. In this phase we have retrieved the user flag and are now looking for a means to escalate our privileges to root, in order to read the root flag
Still, no luck finding anything useful so far, but I got some inspiration earlier in the week from this tweet to run a quick check for capabilities.
The results of this command indicate that we have cap_suid set for the python3 binary. To escalate from the user Nathan to root, I ran a python command that specifies the user id and spawns a privileged shell. The oneliner sets the UID to 0(root) and executes sh. Now we can grab that root flag.
python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
Without that tweet, we could have also searched GTFO bins for a way to escalate with the given capability. https://gtfobins.github.io/gtfobins/python/#capabilities
Summary
We found a web page on the host with exciting information about the environment, including packet captures. That webpage was accessible without credentials.
From this packet capture, we were able to find some valid user credentials that allowed us to SSH onto the machine.
We found a python binary with special privileges/capabilities.
We were introduced to Linux Capabilities and learned how to use a
python3binary withcap_setuidto escalate our privileges from user to root.We used tools:
nmap,TCPFlow, and some Python
Findings/Recommendations
While pwning machines can be interesting, it is essential to think about ways to mitigate the things we exploit. Here are some things I would highlight if I stumbled across this machine on the job:
Password Reuse -
Password reuse is a common pitfall. When users reuse application passwords and OS access passwords, it takes one password leak for an attacker to gain access to all of that user's accounts/devices that use that same password. I would recommend training users to avoid password reuse and use password managers to help them.
Passwordless Security Web Console Access -
I would recommend requiring password authentication to the web console. This web console exposed various details about the machine, such as connection info, IP config information, and packet captures, allowing us to gain valid user credentials.
SSH password authentication -
SSH key authentication is not ALWAYS the most appropriate solution but can be a more secure authentication option. In our scenario, we had gained FTP credentials. If the server had disallowed password authentication for SSH, we would not have connected to the machine via SSH and, therefore, could not escalate our privileges to root. SSH keys are much harder to crack than passwords, and therefore assuming these keys are not leaked somewhere, the SSH path wouldn't have been possible for us.
Remove Capability -
Remove capability on python binary that allows for privileged escalation by using the following command:
setcap -r </path/to/python3>